Information Technology
SoftDocs
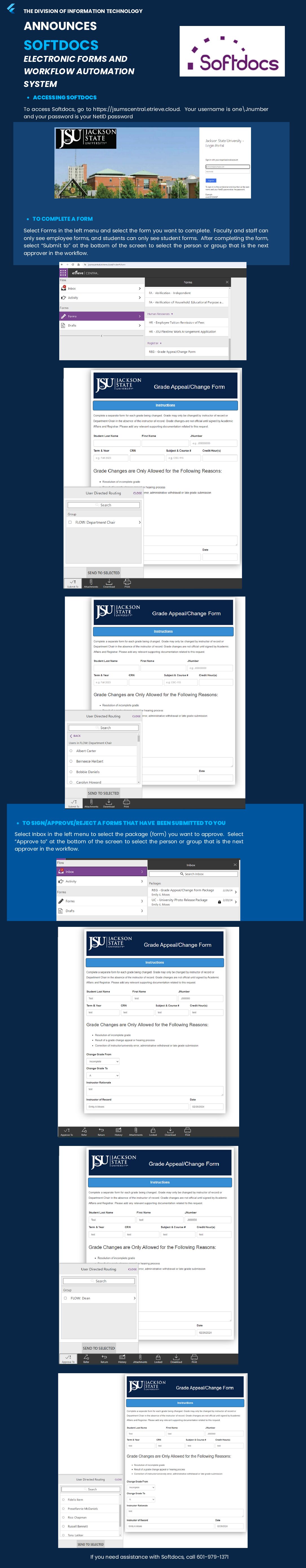
SoftDocs provides an innovative suite of document management and workflow automation solutions specifically designed for the unique needs of universities. With a focus on enhancing efficiency, compliance, and sustainability, SoftDocs offers a seamless way to manage student records, financial documents, and employee paperwork all in one place. Its flagship platform, Etrieve, simplifies document access, streamlines processes through electronic forms and automated workflows, and integrates effortlessly with existing ERP systems. By adopting SoftDocs, universities can significantly reduce paper usage, improve operational efficiency, and dedicate more resources to student success. SoftDocs isn’t just a software provider; it’s a partner in your institution’s digital transformation journey, ensuring a more organized, accessible, and future-ready campus.

PREMIER IT SERVICES
IT services refer to the various types of support and assistance that organizations provide to users of computer and information technology systems. These services can be provided in-house by a company’s IT department, or they can be outsourced to a third-party vendor.
Some common types of IT services include:
- Help desk support: Provides assistance to users who are experiencing technical issues or have questions about how to use certain systems or software.
- Network and infrastructure support: Manages and maintains an organization’s computer networks and related infrastructure, such as servers and data centers.
- Cybersecurity: Protects an organization’s systems and data from cyber threats such as hacking and malware.
- Cloud services: Provides access to data storage and computing resources through the internet, rather than via on-premises hardware.
- Software development: Designs, creates, and maintains custom software applications for an organization.
IT services can be provided on a one-time or ongoing basis, and may be purchased on a pay-per-use or subscription basis. It is important for organizations to have reliable IT support in order to ensure the smooth operation of their systems and to protect against potential cybersecurity threats.
IT Software
Resources

Information Technology